一,基本拓扑
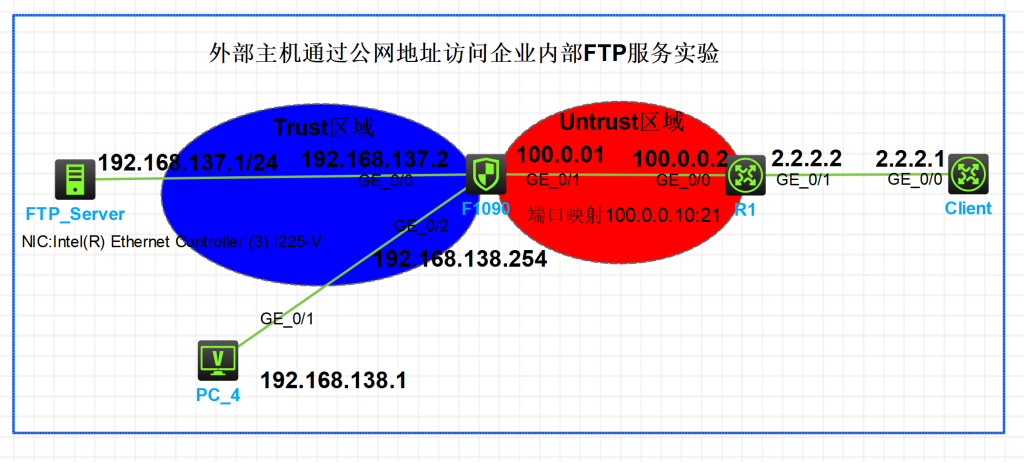
二,配置过程
- 防火墙端口映射配置,设备接口地址配置如下
#
interface GigabitEthernet1/0/0
port link-mode route
combo enable copper
ip address 192.168.137.2 255.255.255.0
manage ping inbound
manage ping outbound
#
interface GigabitEthernet1/0/1
port link-mode route
combo enable copper
ip address 100.0.0.1 255.255.255.0
manage ping inbound
manage ping outbound
#
interface GigabitEthernet1/0/2
port link-mode route
combo enable copper
ip address 192.168.138.254 255.255.255.0
#
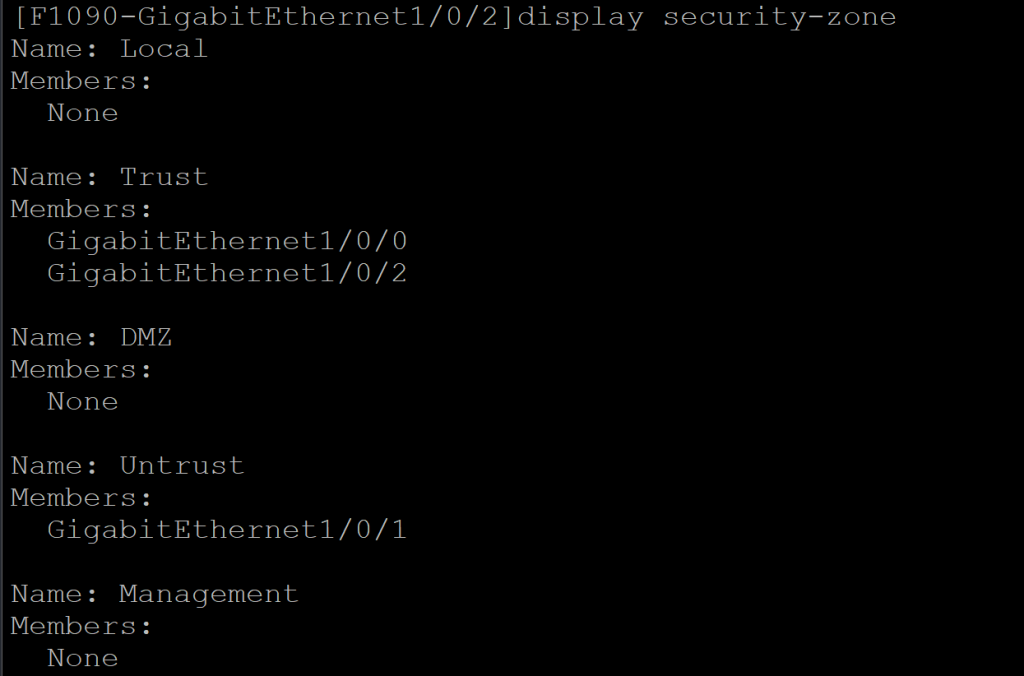
- 防火墙安全区域配置,将接口添加到对应的区域
[F1090-GigabitEthernet1/0/2]display security-zone
Name: Local
Members:
None
Name: Trust
Members:
GigabitEthernet1/0/0
GigabitEthernet1/0/2
Name: DMZ
Members:
None
Name: Untrust
Members:
GigabitEthernet1/0/1
Name: Management
Members:
None
- 配置一条静态路由
#
ip route-static 0.0.0.0 0 100.0.0.2
#
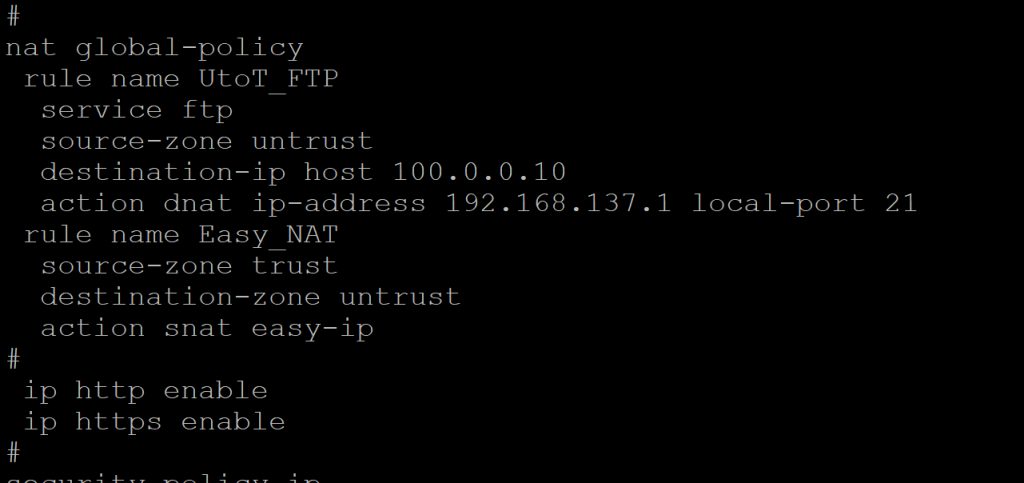
- 在防火墙上配置端口映射
#
nat global-policy
rule name UtoT_FTP
service ftp
source-zone untrust
destination-ip host 100.0.0.10
action dnat ip-address 192.168.137.1 local-port 21
rule name Easy_NAT
source-zone trust
destination-zone untrust
action snat easy-ip
#
ip http enable
ip https enable
#
- 在Client设备配置一条指向FTP_Server的路由
接口地址配置
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 2.2.2.1 255.255.255.0
#
静态路由配置
#
ip route-static 0.0.0.0 0 2.2.2.2
#
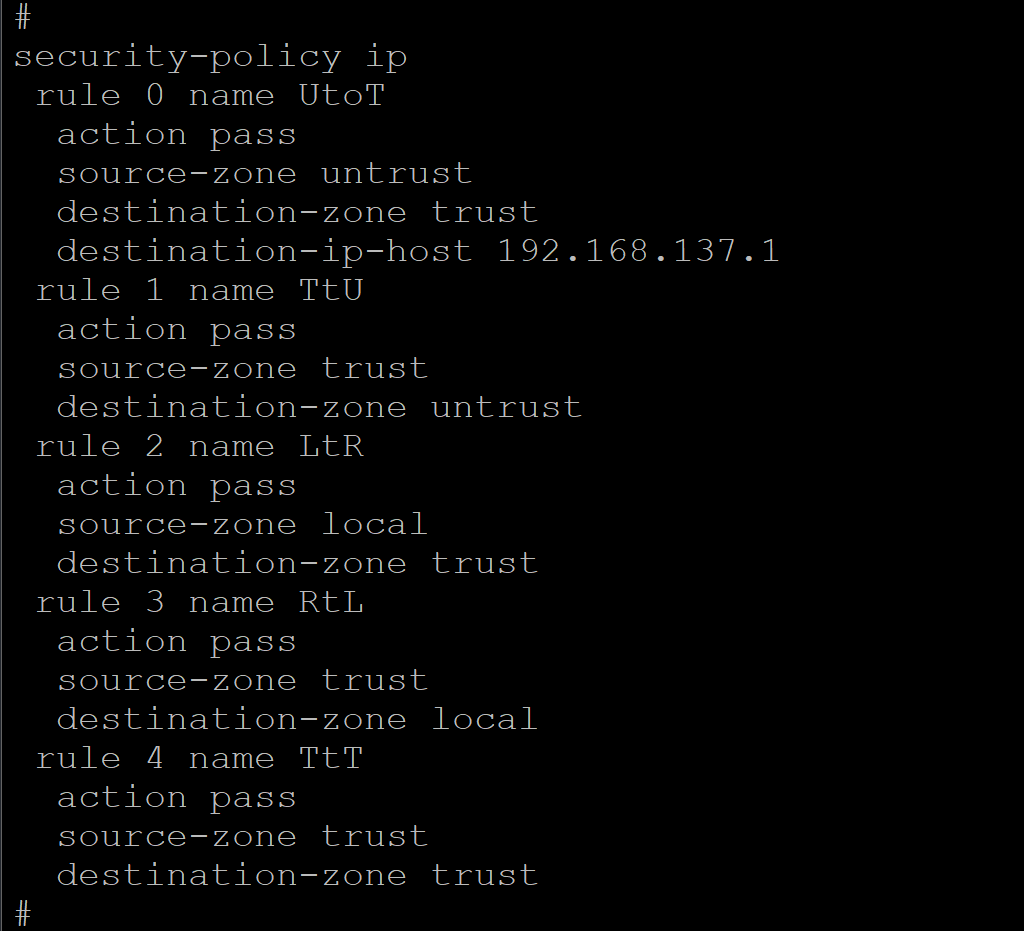
- 防火墙区域安全策略配置
#
security-policy ip
rule 0 name UtoT
action pass
source-zone untrust
destination-zone trust
destination-ip-host 192.168.137.1
rule 1 name TtU
action pass
source-zone trust
destination-zone untrust
rule 2 name LtR #表示local到trust
action pass
source-zone local
destination-zone trust
rule 3 name RtL #表示trust到local
action pass
source-zone trust
destination-zone local
rule 4 name TtT
action pass
source-zone trust
destination-zone trust
#
三,验证测试
- 在Client端访问FTP服务器可以正常登录FTP服务器
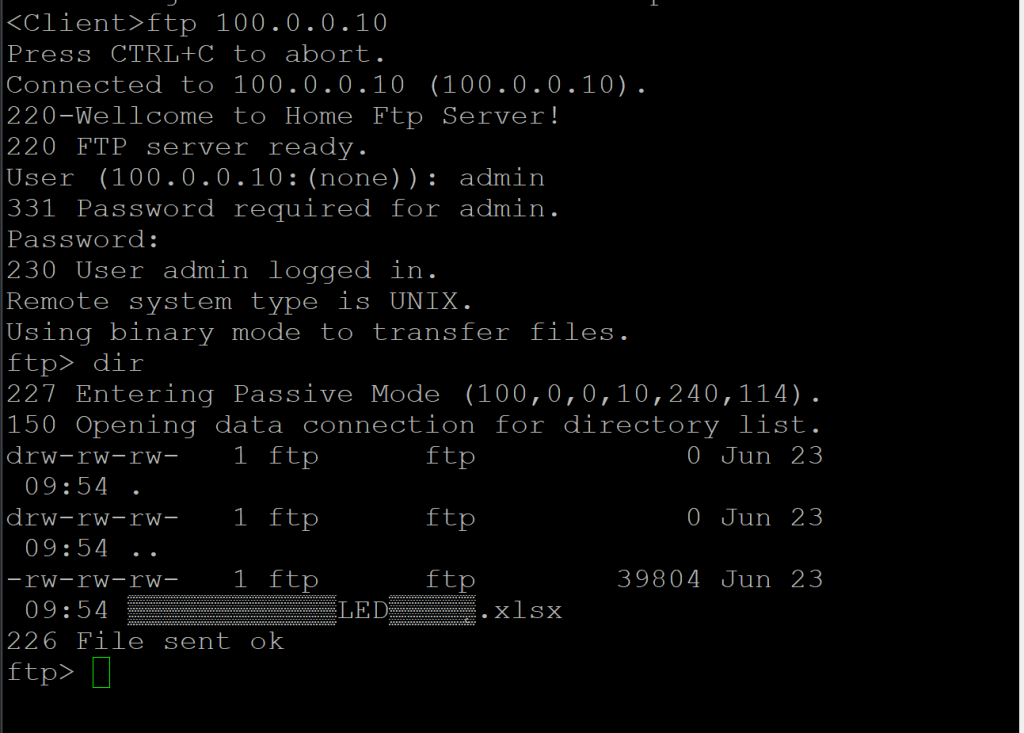
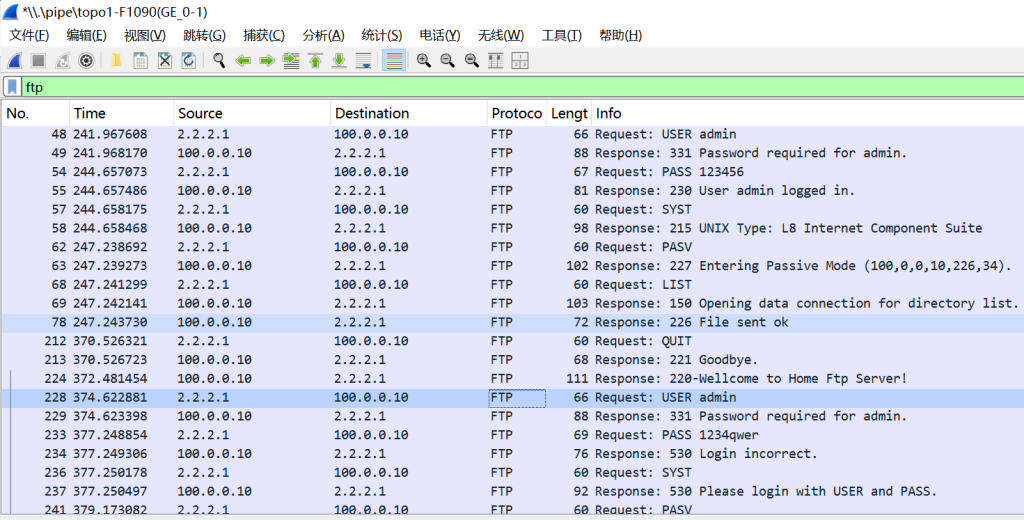
- 在防火墙GE_0/1口抓包如下图:
在防火墙GE_0/0口抓包如下图:
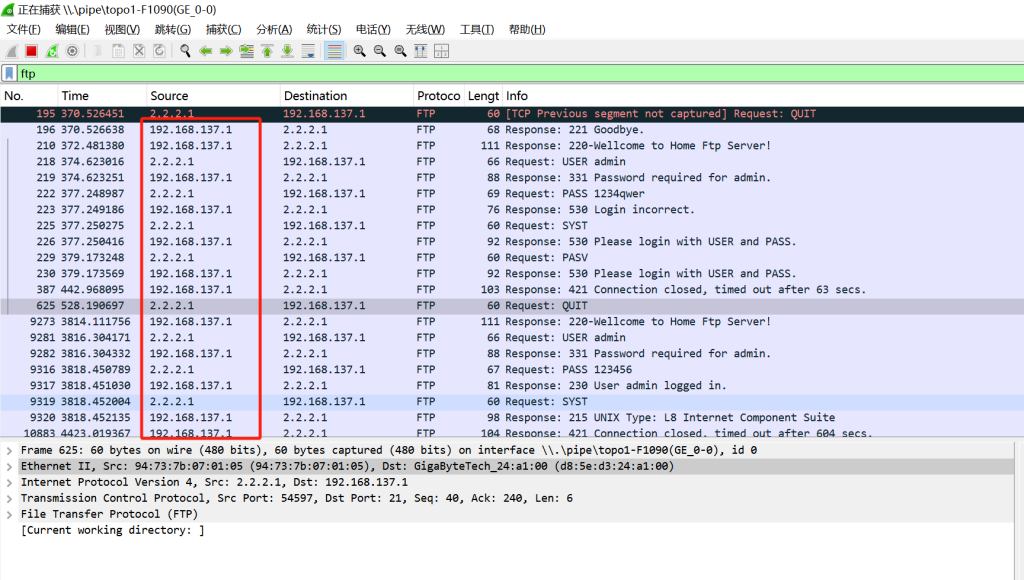
- 从上图可知,地址已经被映射成了192.168.137.1,防火墙配置的这条命令生效了
nat global-policy
rule name UtoT_FTP
service ftp
source-zone untrust
destination-ip host 100.0.0.10
action dnat ip-address 192.168.137.1 local-port 21H3C防火墙在安全域间实例上应用包过滤的ACL典型配置:https://www.hao0564.com/5370.html
