一,基本拓扑
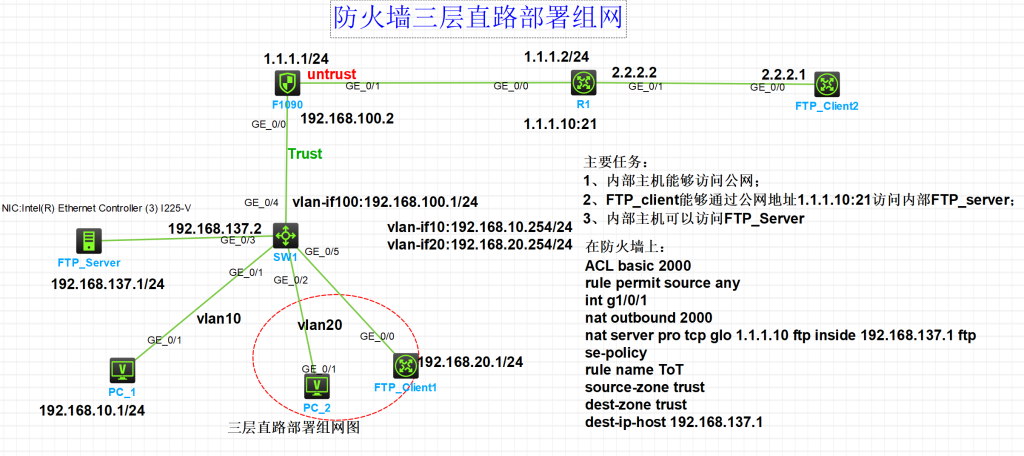
二,配置过程
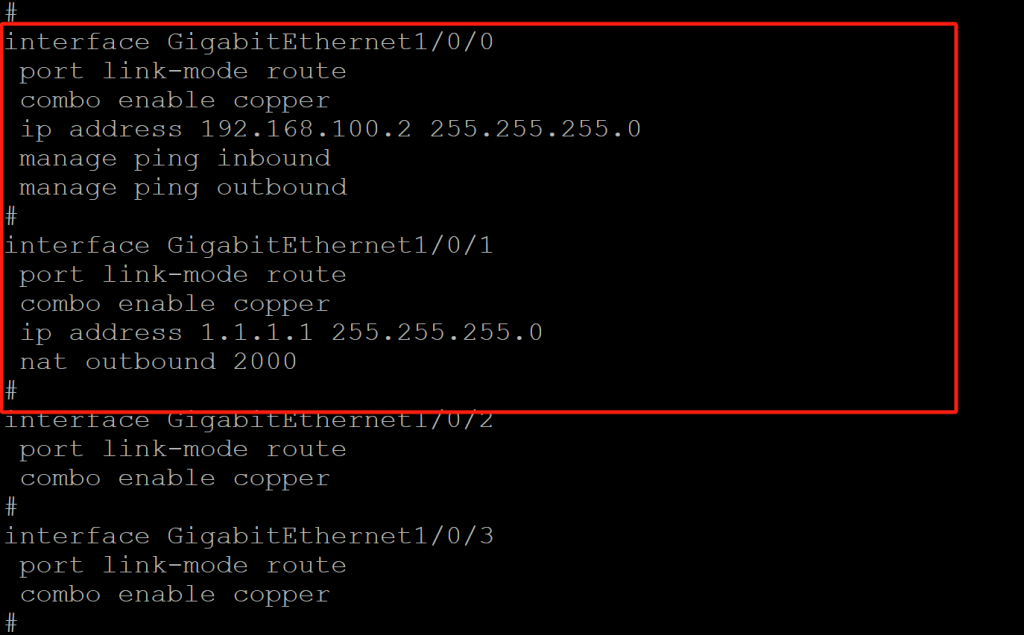
1,防火墙端口相关配置,设备接口地址配置如下
#
interface GigabitEthernet1/0/0
port link-mode route
combo enable copper
ip address 192.168.100.2 255.255.255.0
manage ping inbound
manage ping outbound
#
interface GigabitEthernet1/0/1
port link-mode route
combo enable copper
ip address 1.1.1.1 255.255.255.0
nat outbound 2000
nat server protocol tcp global 1.1.1.10 inside 192.168.137.1 rule ServerRule_1
#
- 防火墙安全区域配置,将接口添加到对应的区域
#
security-zone name Local
#
security-zone name Trust
import interface GigabitEthernet1/0/0
#
security-zone name DMZ
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
#
security-zone name Management
#
scheduler logfile size 16
#
line class aux
user-role network-operator
#
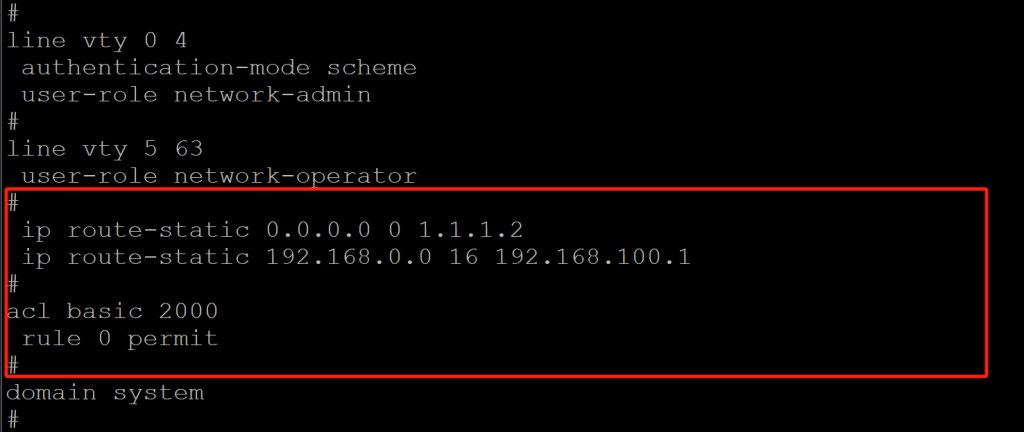
- 防火墙静态路由,NAT配置
#
ip route-static 0.0.0.0 0 1.1.1.2
ip route-static 192.168.0.0 16 192.168.100.1
#
acl basic 2000
rule 0 permit
#
- 防火墙安全区域配置
#
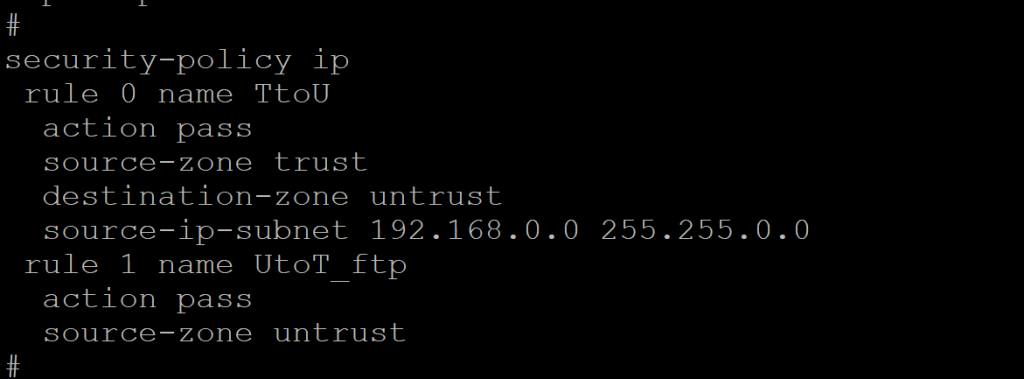
security-policy ip
rule 0 name TtoU
action pass
source-zone trust
destination-zone untrust
source-ip-subnet 192.168.0.0 255.255.0.0
rule 1 name UtoT_ftp
action pass
source-zone untrust
#
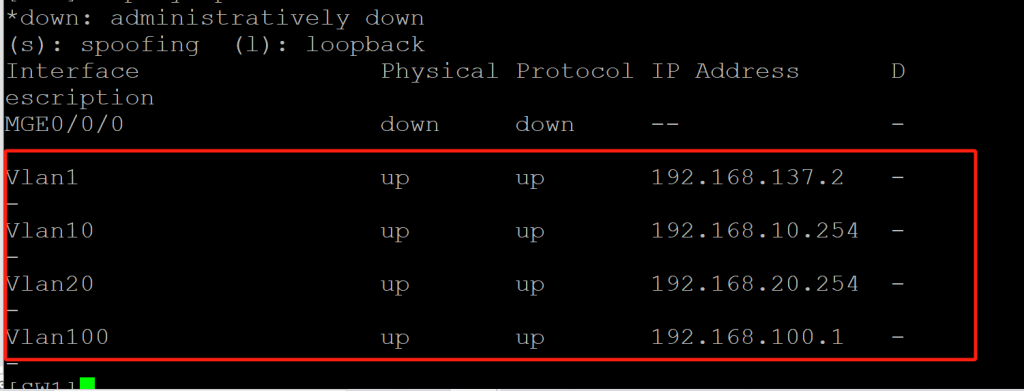
2,交换机相关配置SW1
创建vlan10 vlan20 vlan100,把端口添加到相应的Vlan
#
interface GigabitEthernet1/0/1
port link-mode bridge
port access vlan 10
combo enable fiber
#
interface GigabitEthernet1/0/2
port link-mode bridge
port access vlan 20
combo enable fiber
#
interface GigabitEthernet1/0/3
port link-mode bridge
combo enable fiber
#
interface GigabitEthernet1/0/4
port link-mode bridge
port access vlan 100
combo enable fiber
#
interface GigabitEthernet1/0/5
port link-mode bridge
port access vlan 20
combo enable fiber
#
- 配置vlan三层ip地址
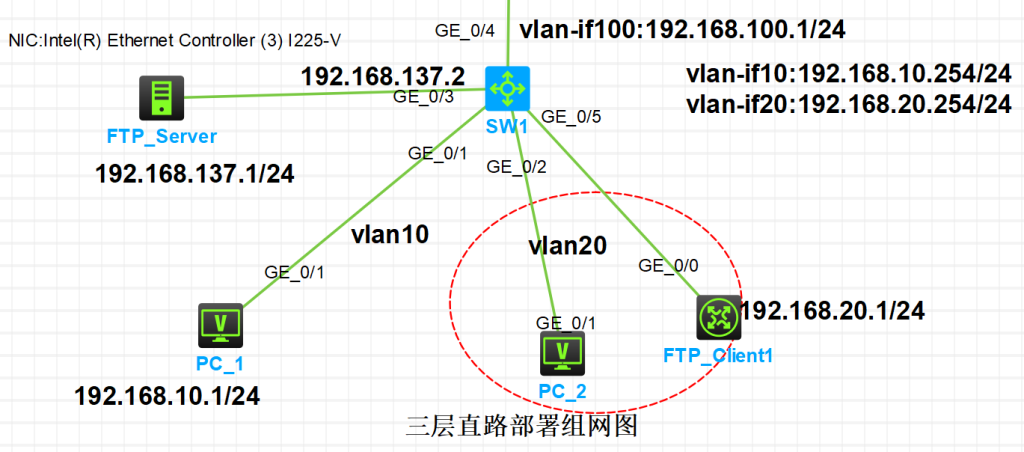
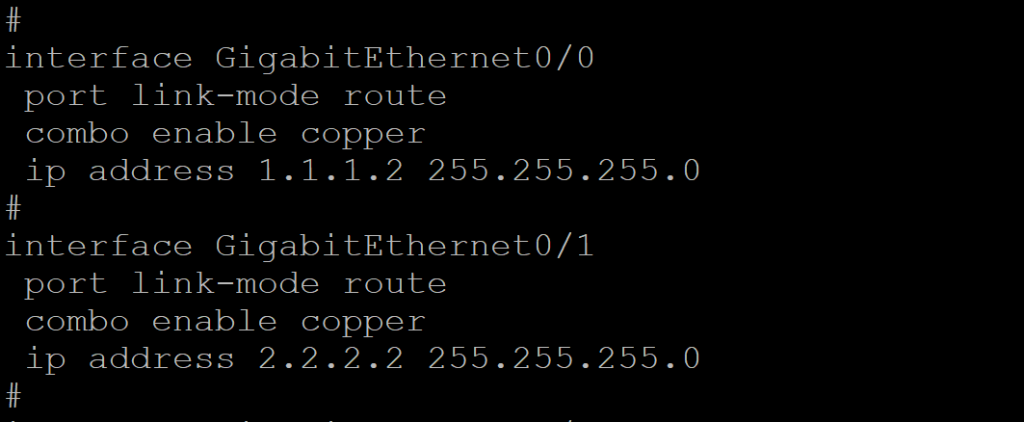
3,路由器R1相关配置
- 路由器接口配置
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 1.1.1.2 255.255.255.0
#
interface GigabitEthernet0/1
port link-mode route
combo enable copper
ip address 2.2.2.2 255.255.255.0
#
4,FTP_Client2相关配置
- 配置接口地址
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 2.2.2.1 255.255.255.0
#- 静态路由
#
ip route-static 0.0.0.0 0 2.2.2.2
#内外FTP_Client1如何通过1.1.1.10访问ftp服务器
- 在防火墙GE1/0/0口配置nat hairpin enable
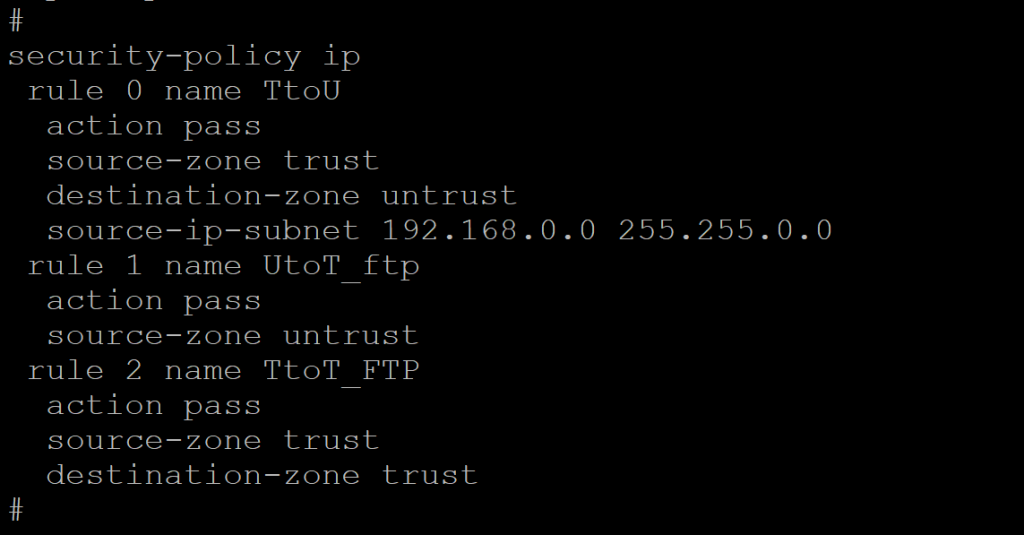
- 在防火墙安全区域添加Trust到Trust
#
security-policy ip
rule 0 name TtoU
action pass
source-zone trust
destination-zone untrust
source-ip-subnet 192.168.0.0 255.255.0.0
rule 1 name UtoT_ftp
action pass
source-zone untrust
rule 2 name TtoT_FTP
action pass
source-zone trust
destination-zone trust
#

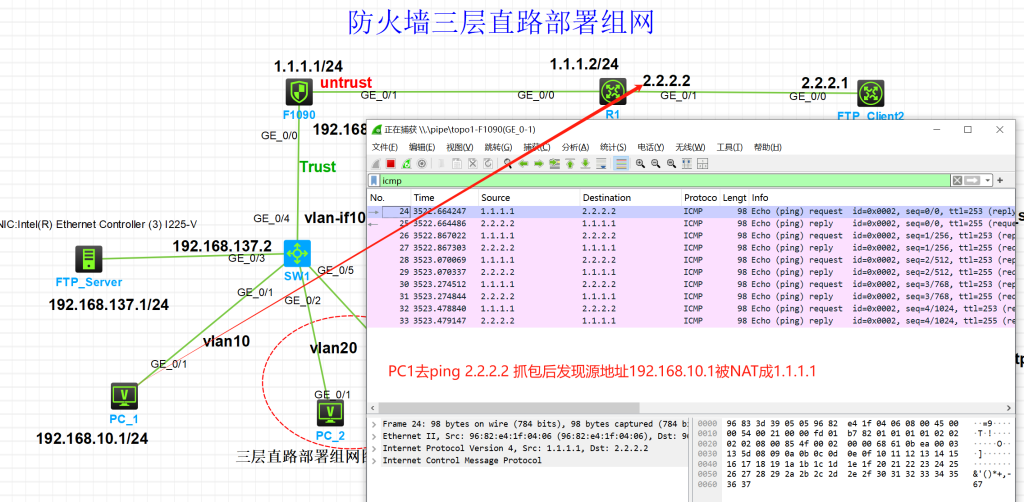
三,验证测试
- FTP_Client2客户端访问FTP_Server
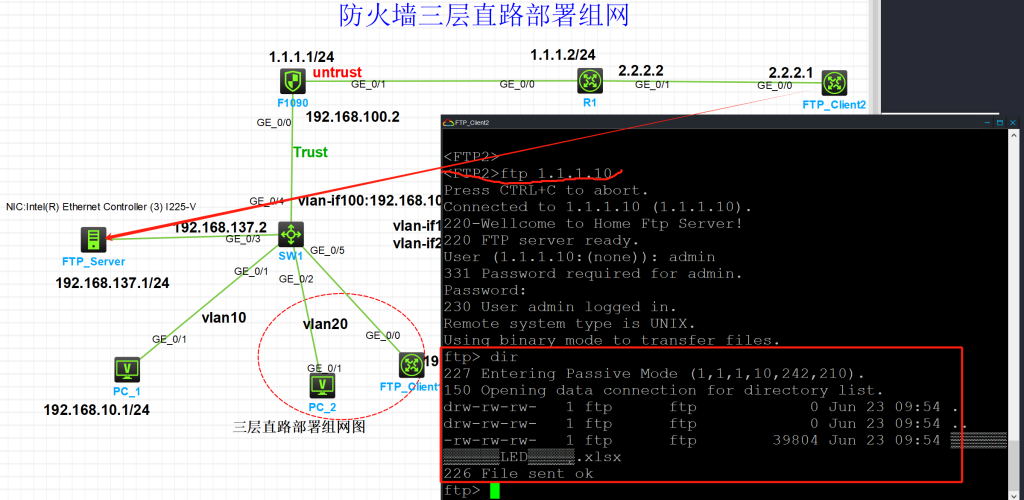
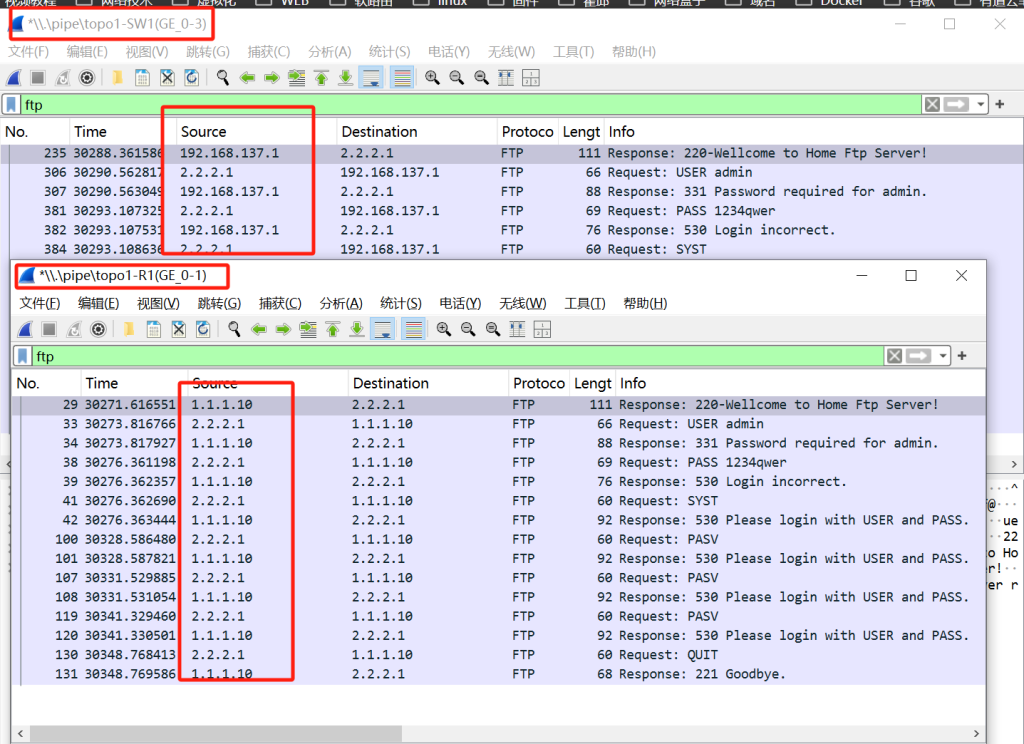
- Wireshark抓包源地址1.1.1.10 被NAT端口映射到192.168.137.1
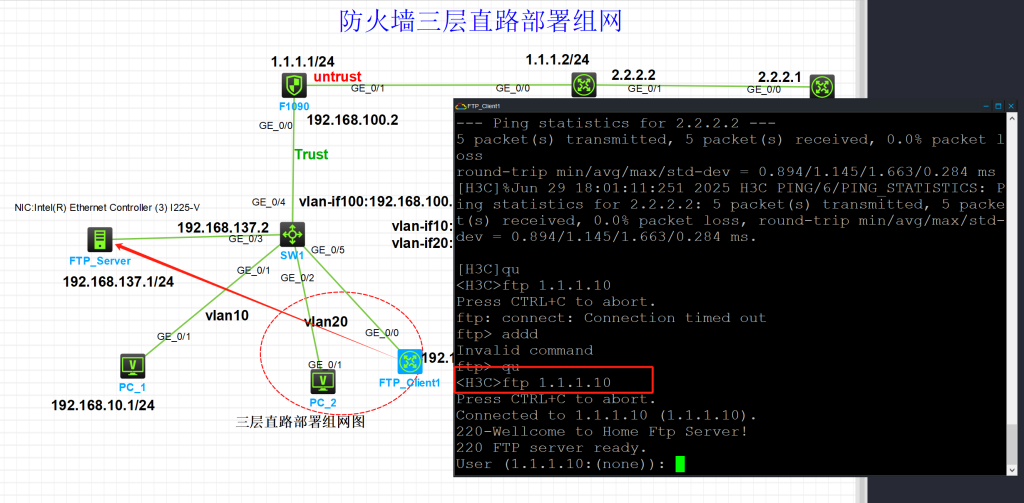
- FTP_Client1通过1.1.1.10访问FTP_Server服务器
外部主机通过公网地址访问企业内部FTP服务实验:https://www.hao0564.com/5390.html
